Back in September 2016 I attended R2con, the first public and international congress about Radare. Needless to say, it was pretty awesome 😀 and I recommend everyone interested in reverse engineering to go there next year. During the conference, Riscure proposed a simple reversing challenge using Radare to play with. You can find the challenge here. This is my (very short and dumb) writeup of it.
The challenge consisted of reversing an ELF binary and figuring out a password. When running the binary, you had to enter the password to get a message saying that you won the challenge. No modifying was allowed, just reversing. Now, this in itself was super easy since it was meant as an introduction, but I didn’t know how to use r2 well enough so it took me a while to solve it. 😀
The first problem I ran into was that it used a different version of libcrypto than my distro so I had to set up a VM. I suppose I could have installed another libcrypto and have them coexist, or used a chroot jail or whatever, but just firing up a VM seemed like the easiest choice to me – especially since I’m already used to Vagrant for this kind of thing.
After that, it was time to fire up Radare:
$ chmod +x RHme2_prequalification_challenge # (did not have the +x bit in Github)
$ ./r2 ./RHme2_prequalification_challenge
Then analyzed everything with the “aaaa” command and launched the UI with “=H” (because I’m lazy). Using the UI I quickly listed the strings, found the relevant ones, then looked for references to them. Turns out everything was right there in main() so this step wasn’t really needed! 😀
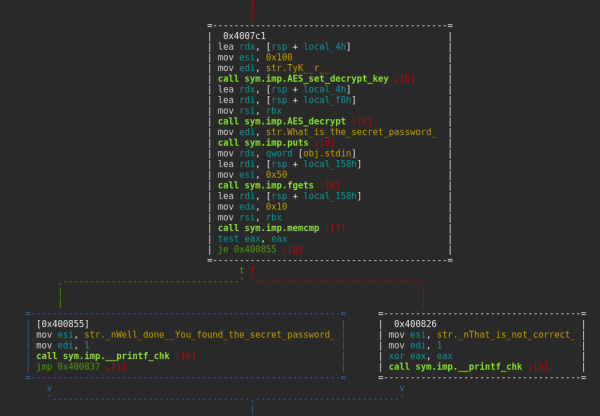
So, going back to the console, using visual mode we can see the code right away:
There was some code before the AES decryption that may be some kind of obfuscation, but I didn’t bother with it statically because it was easier to just put a breakpoint at the memory compare after decryption to see what the hardcoded password was.
Turns out to run Radare as a debugger you need to specify -d before opening the file. I got stuck there for a while because I’m such a n00b. #shame 😀
So, after running “r2 -d”, setting the breakpoint with “db 0x0040081d” then executing the program with “dc”, I got prompted for a password. Just typed anything and continued, after that the breakpoint was hit.
From the code I knew the argument with the decoded password should be in the rbx register, so using the “dbr” command to show the registers, then the “s” command to change the pointer (another odd concept for those of us coming from gdb!) and finally using the “x” command I could see the memory contents:
Running the program again and trying out that password confirmed it was correct. TA-DA!
Well, now that I’ve made you waste your time reading this, here’s a much better writeup for it. Enjoy! 😉 #trolling